PEAK CARES
CUSTOMER SUPPORT
Our Mission
To be the most employee and customer service centered Internet service provider in the industry. We offer ourselves as a resource to our community & provide quality Internet services that help customers achieve their goals through our drive for innovation, service, and reliability.
We are PEAK Internet and we care about you.
Please email us anytime at
peakcares@peakinternet.com
How does Fiber-To-The-Home work?
In the areas that PEAK Internet provides Fiber-to-the-Home, also known as PEAK Fiber, PEAK delivers a physical fiber connection to the home. It will be required for PEAK to install equipment in or on your home to enable this connection to work. Once Fiber has been installed into the home, customers will be capable of having the fastest internet speeds available.
How does Fixed Wireless work?
Fixed Wireless is a type of Internet service that relies on towers located on high points like hills and mountains within your area that we can then pick up with an antenna mounted to your home. We have a great diagram here which shows a visual representation of the basics of fixed wireless service.
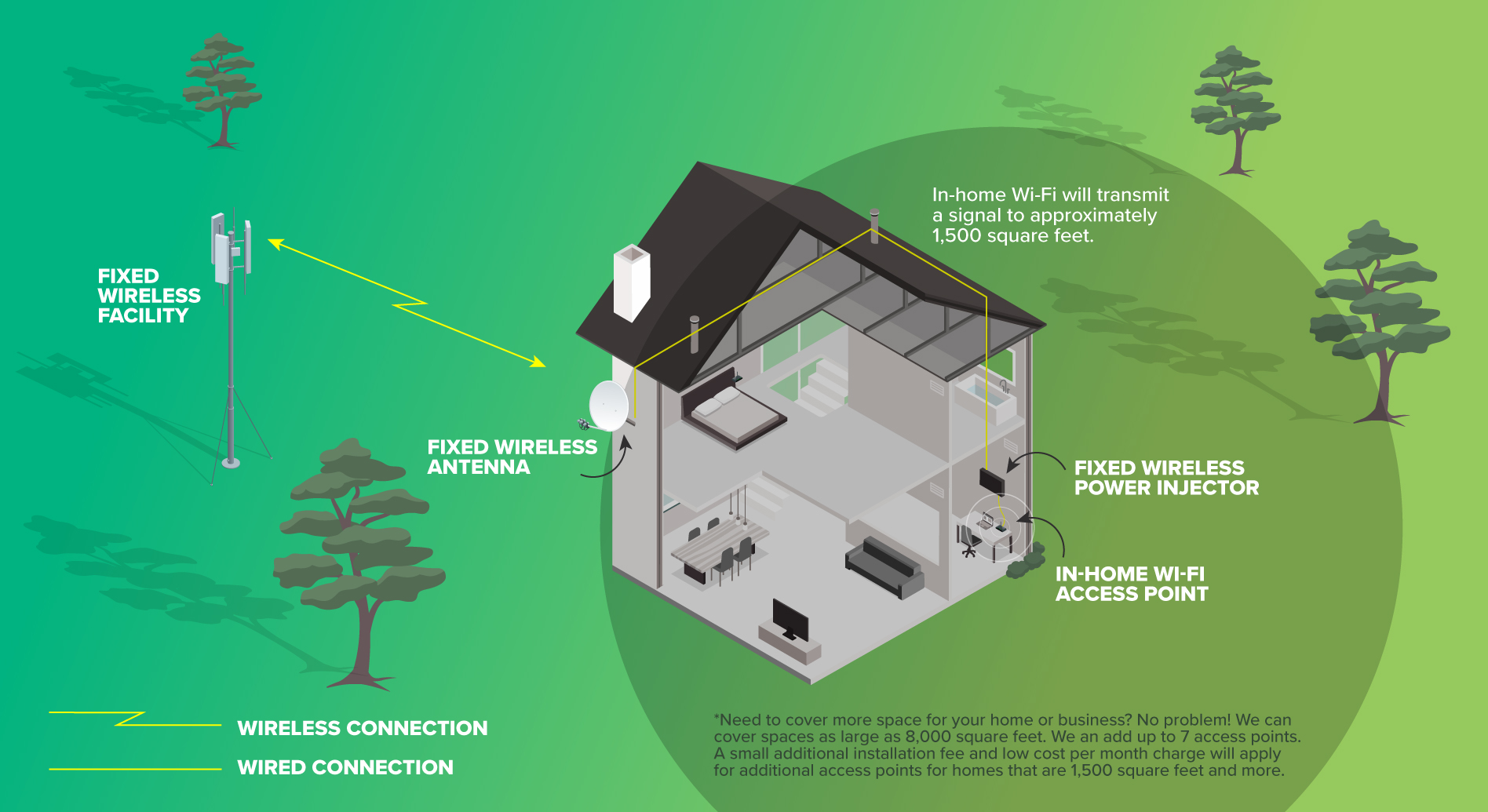
The great thing about this option is that we can offer Internet service to a large area without the need of a traditional cable or phone lines connecting your home.
What kind of plans are recommended for different household sizes?
The type of Internet plan that you choose is highly dependent on you and your families specific use. For the most part PEAK recommends that larger households subscribe to a higher speed tier.
When will I be able to receive Fiber-To-The-Home at my residence? (sub questions like why can’t I get Fiber to my home?)
In order for a customer to be connected to PEAK Fiber, PEAK must have fiber infrastructure in the area. PEAK has a very extensive network, with several areas that we offer PEAK Fiber. To see if your home qualifies use the Order Now tool to check availability. If fiber isn’t available in your area, simply fill out the Interest Form. PEAK uses clusters of Interest to determine future fiber builds.
What is Total Home Managed Wi-Fi and what are the benefits?
The services available vary greatly by area. Please call us to find out Wi-Fi options are available to you!
Call 541-754-7325
Does PEAK have contracts?
PEAK Internet does not require residential customers to sign long term contracts.
Can I save money with PEAK Internet vs. Cable or Satellite?
One of the key differences between PEAK Internet and both cable and satellite providers, is that all of PEAK Internet services include unlimited usage with no data caps. Also we don’t require our customers to bundle several services to get the best prices. We offer the best price possible on an ala carte’ basis. The only requirement is you have to subscribe to PEAK Internet for the other services to work.
What if I rent the residence I reside in instead of owning?
PEAK is always happy to work with your landlord or rental company. We do require that before we install our equipment that we have either written permission or a faxed letter of consent from the landlord or rental company.
What internet speeds are offered through PEAK?
At PEAK Internet we offer service through Fixed Wireless and Fiber connections at different reliable speeds. Follow the links below to view the different speed packages we offer:
Can I watch TV through PEAK Internet?
Yes, our live tv platform gives you all the same programming as a standard cable package, but runs on all your favorite devices such as smartphones, tablets, streaming media boxes, etc.
Do I need to be present for my internet installation?
Yes PEAK requires that a person 18 or older be present during the time of installation. If a contract is being signed then we want the account holder to be present.
How long does an installation take?
An installation will take approximately two hours, please be sure to either have yourself or an approved person on your account present during the installation. If you are interested in receiving service with PEAK Internet please call us at 541-754-7325 or visit either of the links below to get started.
How does fiber connect to my home?
Fiber is connected to a customer’s home via a piece of equipment called and ONT. The ONT is either installed on the outside of the house or in an easily accessible part of the home, such as the garage.
What if I already have an existing service in my home?
Some customers already have PEAK Internet Fixed Wireless Service when we build fiber into an area. These customers can easily convert from fixed wireless to PEAK Fiber.
How much does installation cost for Fixed Wireless?
Fixed wireless installation cost depends on the type of package you go with. With the agreement of a 2 year contract we only charge you our equipment deposit of $99.00 which would be included on your first bill. With a contractless installation we still charge the equipment deposit of $99.00 but we would also include an installation fee of $99.00, both charges would show up on your first billing. Installation costs and service costs are clearly laid out on the fixed wireless section of our website.
How much does installation cost for Fiber?
PEAK Internet’s base fee for fiber installation is $250 for up to 250 ft of aerial construction. Homes with longer drops or that require underground construction will be given an individual proposal for actual installation costs.
How do I connect to my Wi-Fi?
Connecting to Wi-Fi can depend on the type of device you are using. Most devices have either a setting or preference tab where the WI-FI settings for your device are located. From here you can scan for available networks. Once you have located your network name the device will then prompt you to enter either a WPA key or a passcode. If this is the first time you are using your new connection a network name and passcode is provided to you. If you do need further assistance our tech support is available 24/7 at 541-754-7325.
What is a Fiberhood?
A Fiberhood is an area that PEAK has decided to build fiber to. Fiberhoods are established in two ways; the first is developed by PEAK Management to help achieve organizational goals. The second is developed when several prospective customers in an area all submit interest in receiving PEAK Fiber. When there are enough of these interests submitted PEAK will create a Fiberhood and begin the process of building fiber to the area.
How can I check on the status of my Fiberhood?
To check on the status of your Fiberhood, you can go to Fiberhood Watch page and select your Fiberhood to see the status and map, or enter your address to find your Fiberhood.
How can I join Fiberhood Watch?
Joining the fiberhood watch is a great opportunity to see the status of any pending PEAK fiber builds in your area. By submitting interest in our fiber service you can then see the status of any fiber builds in your area. You can also check to see how many of your neighbors have submitted their interest for PEAK fiber. You can submit an interest form here.
Do I need to pay money upfront?
We do not request for you to pay upfront for services, our Customer Service Representatives will work with you to set up a payment plan, you are able to look at via your SmartHub account.
What streaming services are allowed with PEAK Fiber?
With your high speed and reliable connection with PEAK Internet you can access any streaming service of your choice with a compatible device.
Do you have a price guarantee?
All of PEAK’s residential services are offered on a Month-to-Month basis and as such prices are subject to change. However, PEAK has never had a rate increase on our Residential Internet Packages.
Does PEAK engage in the practice of “Speed Throttling”?
No PEAK will never throttle or cap the data transmission of your connection. If your connection appears to not be working as it should call our tech support 24/7 at 541-754-7325.
Are the Internet packages an accurate representation of the upload and download speeds?
Yes, PEAK will make sure to meet or exceed the marketed speeds that you are subscribed to. With our fixed wireless service PEAK will not complete a new installation unless our installer determines that the connection is stable and meets the specifications that we set.
Do I need special equipment to get streaming services?
PEAK Internet provides fast, reliable services to your residence or business, to access streaming services you can connect a device (ex: Apple TV, Amazon Fire) or Smart TV to your PEAK Internet connection.
Can I get your fiber or fixed wireless services in my apartment or condominium?
Yes, PEAK is happy to provide internet options at your apartment or condominium as long as the landlord or rental company allows us to install our equipment. Is it up to the resident to get permission.
How fast is 100 Mbps or 1,000 Mbps?
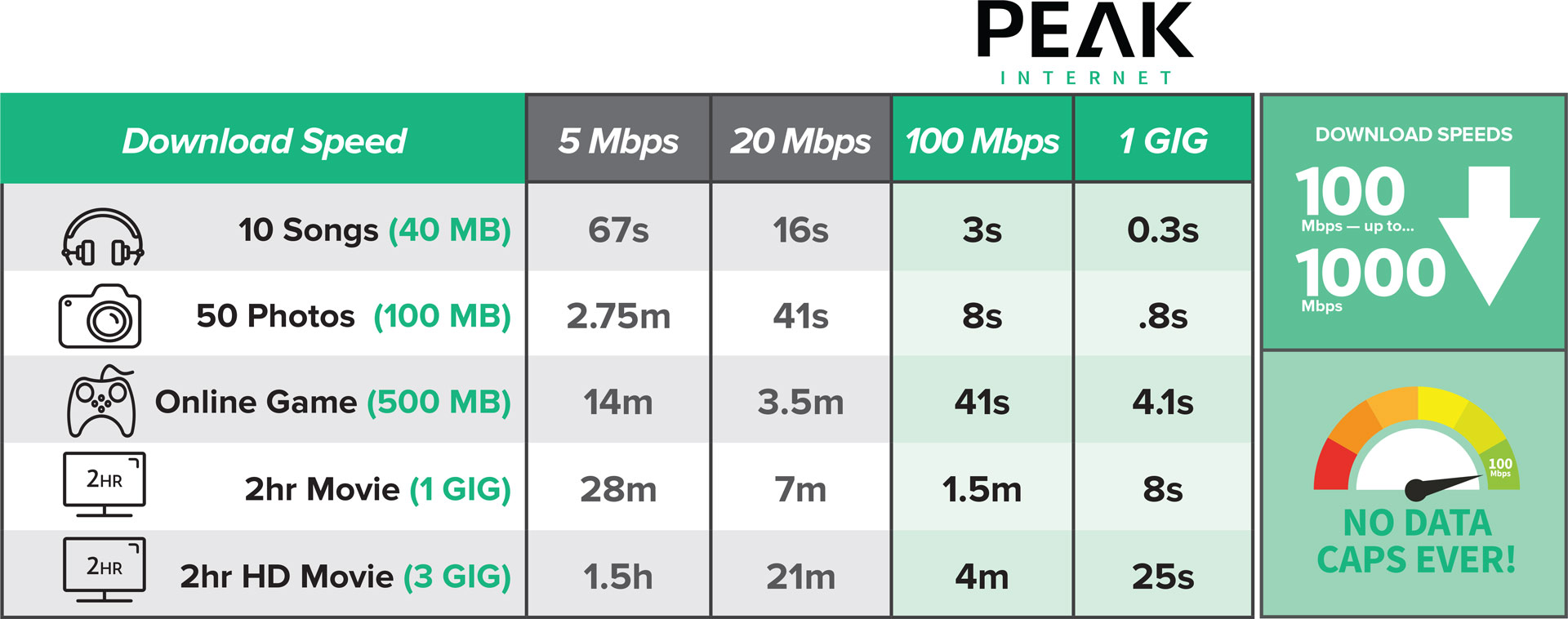
What is the difference between download and upload speeds?
This is a very common question, It is important to know that when speaking of internet speeds Internet Service Providers talk in terms of Megabits per second (Mbps). When comparing different providers pay close attention not only to the download speed (usually the first number), but also the upload speed (usually the second number). Both of these numbers are important and will play an important role in how “good” the Internet Service is you will receive. A download speed takes into account the speed in which you receive data from the internet. For example receiving an email or downloading a movie. Upload speed takes into account the speed in which you send data to the internet. For example, sending an email to your friends or uploading a picture to facebook.
Is telemedicine or virtual medicine made available through PEAK Fiber?
One of the growing trends in the medical industry is Telemedicine. PEAK Fiber offers a very robust connection that will allow customers to utilize this new technology without any issues.
Are there any discounts available for your service(s)?
PEAK has made a decision to offer all of our services at our best price points and not to require bundling to get the best prices. One of the largest complaints about Internet Service Providers in general is that in order to get the best prices they require customers to bundle products together, and many times those customers don’t want or need the additional products. PEAK does not do that! Pick the products that you want and know that you are getting our best price. The only product that we do require that customers buy is Internet Connectivity, as all of our services are based on that product.
Do I need a modem or router for my new PEAK fiber service?
PEAK will provide all the equipment needed to be able to connect your devices to our services.
What is LOS or line of sight?
Line of sight is very important when speaking about our Fixed Wireless product. It is critical that the dish that we install on your home has a clear line of sight to one of our towers. If a tree, a hill, or another building is blocking any part of that view the service will be greatly affected or might not work all together.
What is an ISP?
ISP stands for Internet Service Provider.
Where can PEAK provide internet service?
PEAK provides internet services from just south of Salem to just north of Eugene, and just east of Corvallis to just east of Sweet Home. We utilize two different technologies to serve this large area, Fiber and Fixed Wireless. Fiber is not available in all areas, and customers wanting to see Fiber availability should check out our website for more information. Fixed Wireless while covering a much larger area does have line of sight restrictions, so there may be homes that we can not serve if a clear line of sight can not be established from the home to one of our towers.
Is my credit/debit card information safe once I hand it over to PEAK Internet?
Yes. We take the security of our customers’ private information very seriously. Cards that are used for automatic bill pay in our SmartHub system are in a completely secure system, and periodic security checks are done to ensure the integrity of that system.
Can I get a landline with my PEAK Internet service?
It depends on the service that you are subscribed to. For our fixed wireless service we do not offer a landline option at this time. If you are a PEAK fiber subscriber then yes we do offer a VOIP landline option with all the features you would expect like a voicemail portal, caller ID and more.
Can I continue to use my existing landline number if I switch to PEAK’s phone service?
Yes, PEAK fiber subscribers that choose our landline option will be able to keep their Centurylink or other carriers number if they choose. We would also be happy to provide you with a new phone number if you choose.
What phone features are included with my PEAK landline service?
PEAK’s Voice Services include the following, Local Calling, Long Distance (*Continental U.S. only), Standard 8hr UPS Battery, Voicemail, Caller ID with Name, Call Waiting, Call Forwarding, 3-way calling, and many more. For a full list of features please contact PEAK’s Customer Service Team at 541-754-7325.
Is my PEAK landline service registered with E911?
Yes.
How do I sign up for online bill pay?
Our online bill pay is handled through SmartHub. To access it, click ‘My Account’ at the top of the screen. We have a step by step guide located here to get you started. If you would like step by step guidance over the phone our customer service agents would be happy to help 24/7 at 541-754-7325.
Get Started with SmartHub (My Account)
How can I register?
To get started, you’ll need your account number, last name, and email address.
- Click the “My Account” link at the top of our website and
- Select the link next to “New User?” link at the bottom of the Login Page.
- Setting up a SmartHub account will allow you to view past invoices, set up ACH, Auto Pay, or set up email billing.
- You will need your Account Number, the last name on the account or the business name, and an email address to sign up.
- You will need to validate your account by answering a question about it, then establish two security questions.
- Verify your account with either the amount due from your prior bill, or the zip code associated with the account.
- Once registration is complete, an email will be sent with a temporary password that will be required for your first login. You will be prompted to change this password after logging in successfully.
Setting up AutoPay
Getting started with AutoPay is easy! Once set up, AutoPay will process your payment on the 15th of every month. If the 15th happens to fall on a holiday or weekend, your payment will be processed on the following business day.
- Select Pay my bill
- Select Auto Pay Accounts from the navigation on the left.
- Click the Sign Up for Auto Pay link.
- Select Card or Bank Account and enter your information in order to pay for services each month.
Click the “My Account” button at the top of your screen to give SmartHub a try! If you have any questions or issues, please give our Customer Service a call at 800-731-4871.
Can I pay my bill over the phone?
We are committed to keep you and your information safe and secure, due to this we cannot accept payment over the phone. We offer an easy-to-use system called SmartHub that is safe, secure and can manage your payments.
What is SmartHub?
SmartHub gives PEAK Internet customers the ability to manage their account anytime, anywhere on their mobile device or on the Web. As a PEAK customer, through SmartHub you have the option to pay your bill, check your usage, report service issues and contact us, right at your fingertips.
Does SmartHub have a mobile app?
Yes, Smarthub includes apps for both android and apple. To get the app just search your app store for SmartHub by National Information Solutions Cooperative. There you can register a new account or pay your bill with an existing account. As always if you do need any help call our support center 24/7 at 541-754-7325.
How can I make my bills paperless?
Within SmartHub and under the tab My Profile there is an option to enroll you in our paperless billing service. You can receive your bill via any valid email address that you choose. You can also call our customer service department 24/7 at 541-754-7325 and they would be happy to make this switch for you.
Fiber
If you are having connectivity issues with your fiber connection, please call customer service at this time. 541-754-PEAK (7325)
Fixed Wireless
If you think that your Fixed Wireless connection has failed, the first course of action is to perform a power cycle of your home network, to rule out any local issues. Power cycling in this manner is better, as it allows any connection that previously existed to completely drop, and takes into account the time it may take for a new connection to be created before you attempt to connect.
- Unplug the power cords to your POE and your router if you have one.
- Wait a full three minutes, and then plug in your POE back into power.
- Wait a full two minutes, and then plug in your router.
- Wait thirty seconds and then check your connection for connectivity.
If this basic troubleshooting does not resolve your problem, try another device or power cycle the device you are using to try and connect, or give us a call!
Dial-Up
Dial-up is an olderservice that is primarily used as a backup connection, or where no other options are available as the internet really isn’t developed for dial-up anymore.
- Restart the computer.
- Check the line for dial-tone, remove any splitters that may be between the computer and the jack.
- Confirm that the line from the modem to the wall is in good condition and shorter than six feet. Ensure that both ends are not corroded, and clip firmly into the back of the computer and the wall jack. If your dial-up modem has two ports, ensure you are selecting the one for the modem.
If you find yourself frequently disconnecting from dial-up, disable any Call Waiting features you may have on the line, as these will interrupt your session.
If you need additional help troubleshooting, give us a call!
Wi-Fi Signal Interference
So many of our favorite devices require solid wireless connectivity to be their best, but not all of the corners of your home are wireless-friendly.
Diagnosing Wireless Interference
Wireless interference can have many symptoms. Maybe your audio is choppy, delayed or cutting out during your web meetings. Perhaps you can’t stream videos from the den, or you’ve noticed that your phone can’t connect to the wireless when you’re in the kitchen or the Roku in the kids’ room takes forever to load channels.
These are things that may indicate that wireless interference is affecting YOU. There are a number of complicated and time-consuming solutions that you could try to resolve the issue. You could wire your entire home for ethernet connectivity, or install expensive range extenders… OR you could let us solve the problem for you.
Our Total Home Premium managed wireless solution is installed by professionals who can heat-map your entire home and determine the best placements to access points and customize your in-home personalized wireless solution.
Password Security
Using strong and secure passwords is important to keep your account secure. Use a different password for each of your accounts and avoid re-using passwords.
If someone guesses the password for your Netflix account, and you’ve used the same password on your email and banking accounts, that person could potentially gain access to everything.
Create a unique password that is unrelated to any personal information and uses a combination of upper and lower case letters, numbers and symbols and have your password be more than eight characters in length. Avoid using simple words or phrases like “password” or “letmein” and avoid using keyboard patterns like “qwerty” or “1234”. Sequential patterns like “abcd1234” or “12341234” make your password easier to guess.
One of the more common ways to create a password is to select a random words or phrase, then jazz it up with capital letters, numbers or symbols.
For this example I have selected the words Potato and Flake, and jazzed my password until it is P0t8oh-!f|aKe.
Once you have created a strong password, keep it safe. Writing your passwords down isn’t very secure or any good if you lose track of what you’ve written it on. If you can’t keep track of your passwords, give a password manager like our PasswordGenie a try.
Phishing and how not to get caught
Scammers use a wide variation of tactics to try and trick you into giving them your personal information. They want to trick you into giving them your passwords, account numbers, or other sensitive information that they can use to gain access into your accounts.
Oftentimes you’ll receive a message that looks like it is a company you know or trust. It may say that it is a Social Media site, your bank, credit card company, delivery service or an online store. Be suspicious of any email you receive that you are not expecting.
Sometimes an email just doesn’t look right. Maybe it is formatted strangely, the grammar is awkward or there are spelling mistakes. Maybe the logo isn’t centered or it just doesn’t look or sound like other emails from the same source. Trust your instincts here!
Phishing emails always have a call to action that encourages the reader to take action IMMEDIATELY. This is the second red flag!
If an email has a link that asks you to fill out information hover over the link to check where it is going. Pay close attention to spelling, facebook.securetee.com is NOT the same as facebook.com. You can also avoid links altogether by using your bookmarks!
If an email gets caught in the spam filter and you were expecting it, feel free to release it. If an email you weren’t expecting gets caught in the spam filter, take a good look at it. If the email was sent by a friend, make sure that the “reply to” is the correct email address before responding.
And if you ever have any question, we’re happy to put our eyes on an email and do our best to verify authenticity.
Infected with Malware or Virus?
If you think you’ve been infected with malware or a virus, the best thing to do is to isolate that computer from any network immediately – unplug the ethernet cord or disconnect from the wireless connection. This will prevent anything new from being installed or gathered from the machine.
Once the computer has been isolated from the internet and anything on the network, it is time to look into recovery. Your path forward here depends on how bad the infection is, and how it is affecting the computer. Some bad infections require a computer technician and potentially a reinstallation of the operating system, while other infections can be handled by our Tech Home and Total Tech services.
Once your computer has been recovered, we recommend a good security suite like our Tech Home package to help lock your computer down. Once you have the Tech Home service installed, Total Tech can help you remove infections.
Backing up your website
Backing up your website helps prevent data loss if anything unfortunate occurs. Backups are especially important if your site is built on a Content Management System like WordPress where you also have a database to worry about too.
Backing up your website will prevent the loss of all the work you’ve put into your site, prevent the investment of time or funds to rebuild, and reduce any revenue lost during downtime.
There are multiple ways to backup your site,
Manual Backups
Manually download all files and backup your database to a computer, and then zip it for storage on a local machine or in cloud storage.
Backup Manager
Both Plesk and CPanel have a built-in backup manager and will backup both the files and database, but storage is defaulted to the hosting platform and may not always have external storage options. This also uses storage from the hosting package, so you may need to go in and prune backups from time to time.
Backup Plugin
If you have a CMS like WordPress, you can choose one of the many backup plugin options that exist with both free and paid plugins. The bonus to this is that you can store locally on the hosting platform, or use cloud storage for your backups.
Whatever backup method you use, these should be done regularly. A site that changes frequently should be done more often, but if your site goes weeks to months without changes, you can get away with doing a backup every couple of months. It is also good practice to run backups.
In the event your backups fail, Peak does have access to backups and may be able to assist with the restoration of your site.
WordPress
Setting up SSL
HTTPS or Secure HTTP is an encryption method that secures the connection between your user’s browser and the server your site is hosted on. This makes it harder for hackers to reach your customers through your website.
Any site without an SSL Certificate will be marked as not secure, and may miss out on SEO benefits, or leave your customers or readers with a bad impression.
Before you get started, back up your content and database.
Start off by either setting up Let’s Encrypt, or requesting an SSL Certificate from Customer Service.
To set up Let’s Encrypt for Plesk:
- Log into your Hosting Panel.
- Select Let’s Encrypt.
- Enter your email address in the Email Address field.
- Select the checkboxes for the following Select what else can be secured options:
- Include the “www” subdomain for the domain and each selected alias
- Issue a wildcard SSL/TLS certificate.
- Click the Install button.
- The next screen will add a record to DNS. If you manage your DNS outside of the hosting package, you will need to add this record before you continue.
- Click the Continue button. If the next page gives you an error, repeat the steps above.
To set up Let’s Encrypt for CPanel:
- Log into your hosting panel.
- Select SSL/TLS Status
- Check everything and click the Run AutoSSL.
If you have any issues with this process, we can help you up to this point.
Use a Plugin to do the rest
You can use a WordPress plugin instead of a number of manual steps. Using something like Really Simple SSL is easier. Feel free to use any other SSL plugin if you’d rather.
- Download Really Simple SSL, there is a base edition.
- Log into WordPress
- Install the plugin and activate it.
This should make the SSL Certificate work on your site. You may see that there is mixed content – this is usually where something has been hard-linked and will need to be fixed manually but can also be caused by settings in other plugins.
Protecting your Installation & The Importance of locking it down
Once you have your WordPress site set up the way you want it, locking it down will help you keep it secure.
Install a security plugin
Installing a security plugin can help you lock down your WordPress installation and usually come with a full kit of recommendations to secure your content. If you do one thing, install a security plugin!
Lock down the Theme Editor
The Theme Editor in WordPress is an extremely powerful tool because it gives access to any of the code in your website. We recommend disabling this completely when not in use, as hackers can use this to access any of the data in your site, or use it to attack other sites or distribute malware. If you’re not using the theme editor, it is good practice to lock it down.
You can disable the Theme Editor by adding the following code to the .htaccess file:
define( ‘DISALLOW_FILE_EDIT’, true );
Limit Login Attempts
Limiting login attempts can prevent a hacker from brute forcing the password. This will block their IP for a temporary period of time based on settings that you define/
This will need to be done by installing a plugin, but is also easily bypassed if a hacker is using a VPN.
Adjust file permissions on the wp-config.php and .htaccess files
Adjusting the file permissions of the wp-config.php and .htaccess files can help prevent an attacker from gaining access to your installation. This should be done by an experienced individual, as you can quickly take down your functioning website by setting the wrong permission type.
Some plugins will require different levels of permissions for these files, so your settings may differ.
Disable XML-RPC
The XML-RPC file allows posts from a WordPress app on a mobile device and permits trackbacks and pingbacks. This can be used as an attack vector if an attacker finds a vulnerability.
Be aware that some plugins DO use this, so only disable if it isn’t in use.
To Disable XML-RPC, add the following code to your .htaccess file:
# Disable WordPress xmlrpc.php
<Files xmlrpc.php>
order deny,allow
deny from all
allow from xxx.xxx.xxx.xxx
</Files>
If you want to allow access from a specific IP, replace allow from xxx.xxx.xxx.xxx with the IP address, otherwise remove this line.
Click here to see videos about what you can do with the PEAKZone App.